Cloud Security Managed Services: 2026 Partner Selection Guide
Cloud security managed services are transforming how organizations protect their digital assets in an increasingly complex threat landscape. As cyber threats evolve and regulatory requirements tighten, businesses are turning to specialized providers for comprehensive protection. This shift reflects a broader trend toward outsourcing critical security functions to experts who can deliver 24/7 monitoring and rapid response.
Many organizations struggle with internal resource limitations and skill gaps. Consequently, partnering with experienced providers offers access to enterprise-grade security without the overhead of building in-house teams. Additionally, these services integrate seamlessly with existing managed cybersecurity services to create layered defense strategies.
This guide explores how managed cloud security services work, what they protect, and how to choose the right provider for your needs.
What are Cloud Security Managed Services?
In our previous discussion about cyber security managed services, we explored how organizations outsource security operations to specialized providers. Cloud security managed services represent the natural evolution of this model, specifically designed for cloud environments. While traditional managed security focuses on on-premises infrastructure, cloud-specific services address unique challenges like multi-cloud complexity and dynamic resource scaling.
Organizations implementing managed cloud security services gain immediate access to specialized security teams and enterprise-grade protection. These services monitor cloud workloads across AWS, Azure, Google Cloud, and other platforms. Moreover, they provide continuous threat detection tailored to cloud-native architectures and serverless applications.
What Cloud Security Managed Services Include
Security operations require continuous attention that many organizations cannot maintain internally. Therefore, managed security services for cloud deliver comprehensive protection through specialized teams and advanced tools. Businesses leverage their benefit from proactive threat hunting and rapid incident response.
Core service components
- 24/7 security monitoring and threat detection
- Incident response and forensic analysis
- Vulnerability assessments and penetration testing
- Security configuration management
- Compliance reporting and audit support
- Identity and access management (IAM)
These cloud security managed services operate through a combination of human expertise and automated technologies. Moreover, providers leverage threat intelligence feeds to stay ahead of emerging attack vectors.
The Difference Between In-House and Managed Security
Building internal security capabilities demands significant investment in both personnel and technology. In contrast, managed service providers for cloud security offer immediate access to seasoned professionals.
| Aspect | In-House Security | Managed Services |
| Staffing | Requires hiring, training, retention | Instant access to expert teams |
| Coverage | Limited to business hours | 24/7/365 monitoring |
| Technology | Capital expenditure for tools | Included in service fee |
| Scalability | Slow to scale up/down | Flexible based on needs |
| Expertise | Limited to team knowledge | Access to diverse specialists |
When to Consider Outsourcing Security
Not every organization needs to outsource their entire security function. However, specific scenarios make these services particularly valuable. Understanding when to implement cloud security managed services helps businesses maximize their security investments.
Consider managed services if you
- Lack internal security expertise or struggle with hiring
- Need 24/7 monitoring but cannot staff overnight shifts
- Face strict compliance requirements (HIPAA, PCI-DSS, SOC 2)
- Manage multi-cloud environments across AWS, Azure, or GCP
- Want predictable security costs versus variable staffing expenses
How Managed Security Services Address Cloud Security Challenges
Organizations moving to the cloud encounter unique security complexities that differ significantly from traditional on-premises environments. Managed cloud security services tackle these challenges through specialized knowledge and proven methodologies. Hence, implementing them enables businesses to overcome resource constraints while maintaining robust protection.
Multi-Cloud Environment Complexity
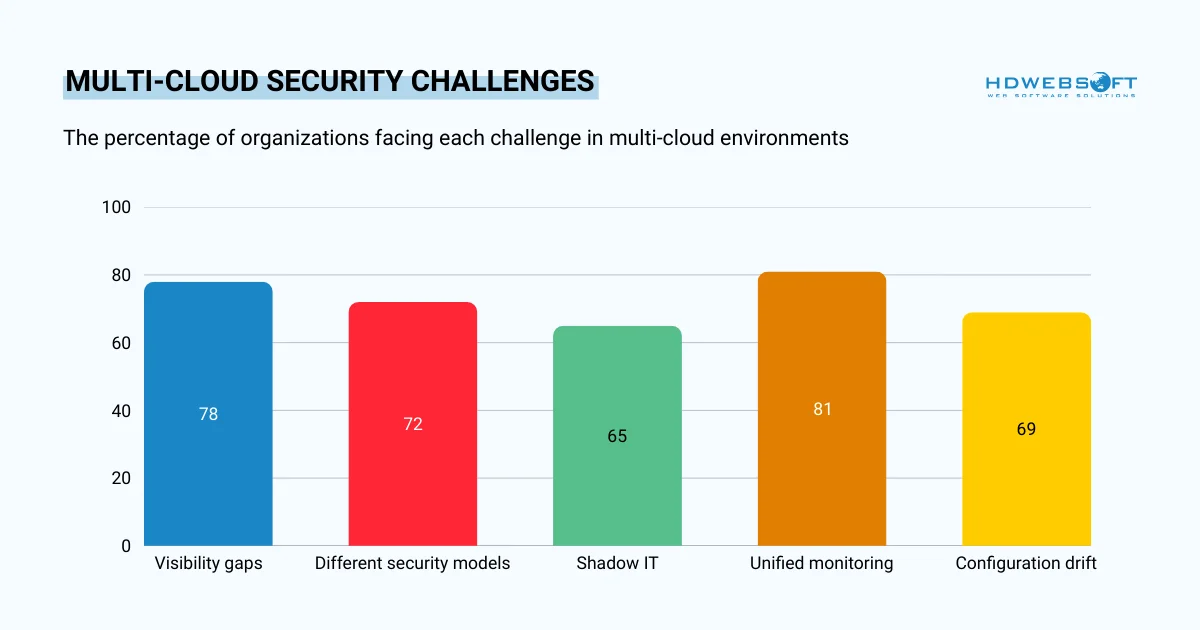
Operating across multiple cloud platforms creates visibility gaps that attackers can exploit. Each provider uses different security controls, making unified protection difficult. For instance, AWS, Azure, and Google Cloud each employ distinct security models and terminology.
Providers of cloud security managed services implement centralized security orchestration across your entire cloud footprint. Furthermore, they normalize security data from disparate sources into actionable intelligence. This holistic approach ensures no assets slip through the cracks.
Shadow IT compounds these challenges when departments deploy cloud resources without central oversight. That’s part of the reason why security teams often discover unauthorized workloads only after incidents occur. Providers use cloud security posture management tools to maintain complete asset inventories. Additionally, they establish governance frameworks preventing unauthorized cloud deployments.
24/7 Threat Monitoring and Response
Cyber threats don’t follow business hours, yet many organizations cannot maintain round-the-clock security operations. Attackers frequently launch campaigns during weekends and holidays when defenses weaken.
Continuous monitoring provides
- Real-time detection of suspicious activities
- Immediate incident response to contain breaches
- Automated threat hunting across cloud workloads
- Correlation of security events across multiple systems
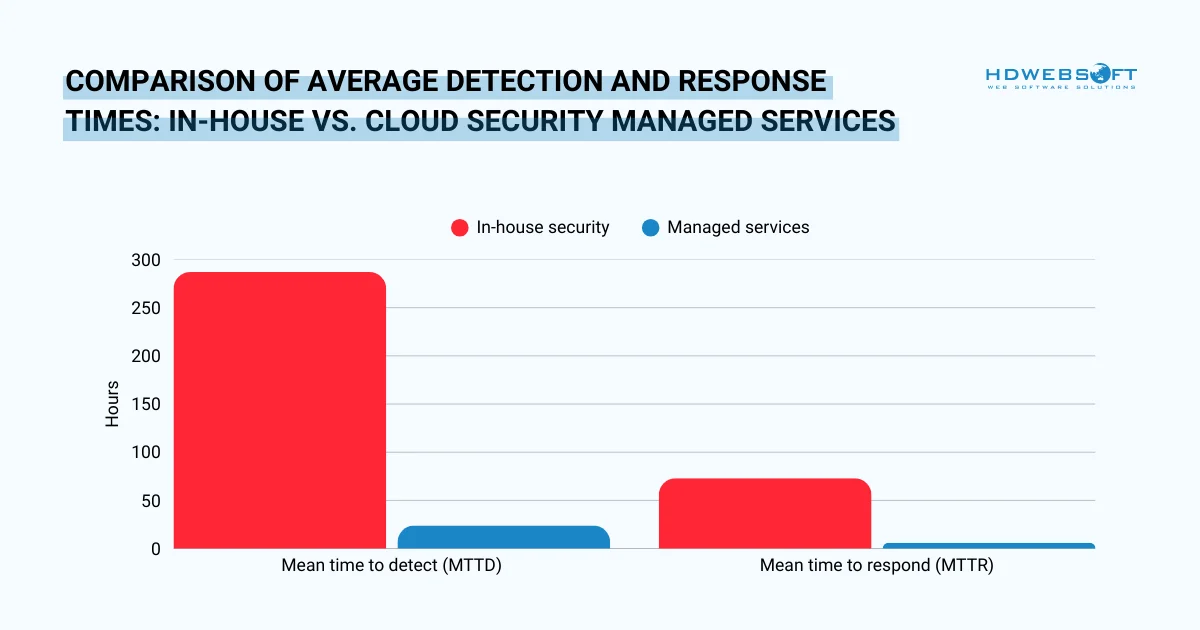
Security operations centers (SOCs) staffed by cloud security managed services watch your environment constantly. Consequently, mean time to detection (MTTD) and response (MTTR) decrease dramatically.
Solving the Security Skills Shortage
The cybersecurity industry faces a massive talent gap with 4.8 millions of unfilled positions globally. Thus, competing for scarce security professionals drives up salaries and extends hiring timelines.
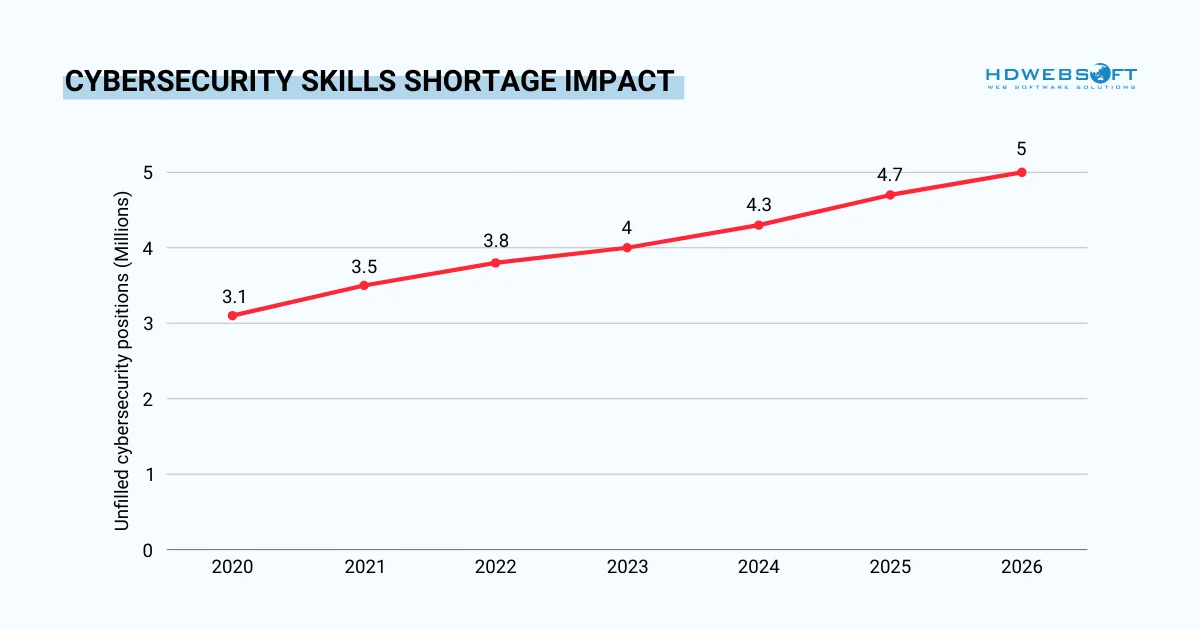
Outsourcing eliminates this struggle by providing instant access to diverse specialists. Additionally, you gain expertise in areas like threat intelligence, forensics, and compliance without individual hires. These teams continuously train on emerging threats and new cloud security technologies.
Threat Intelligence and Proactive Defense
Modern security requires understanding attacker tactics, techniques, and procedures (TTPs) before they impact your environment. Managed service providers for cloud security maintain extensive threat intelligence programs feeding into defensive strategies.
Providers subscribe to commercial threat feeds while contributing to information-sharing communities. This collective intelligence reveals emerging attack patterns targeting specific industries or technologies. Teams from cloud security managed services correlate these indicators with activity in your environment to identify potential compromises early.
Furthermore, threat hunting proactively searches for signs of sophisticated attackers who evade automated detection. Unlike reactive monitoring, hunters assume breach and look for subtle anomalies indicating presence. Weekly hunting exercises examine user behavior, network traffic, and system logs for suspicious patterns. As a result, these efforts often uncover threats residing undetected for weeks or months.
Compliance and Regulatory Requirements
Meeting industry regulations requires deep knowledge of complex frameworks and continuous documentation. How managed service providers ensure secure cloud storage often centers on maintaining compliance across multiple standards.
Providers help with:
| Compliance Area | Managed Service Support |
| Documentation | Automated evidence collection and reporting |
| Audits | Pre-audit assessments and remediation guidance |
| Controls | Implementation of required security controls |
| Training | Security awareness programs for staff |
| Monitoring | Continuous compliance validation |
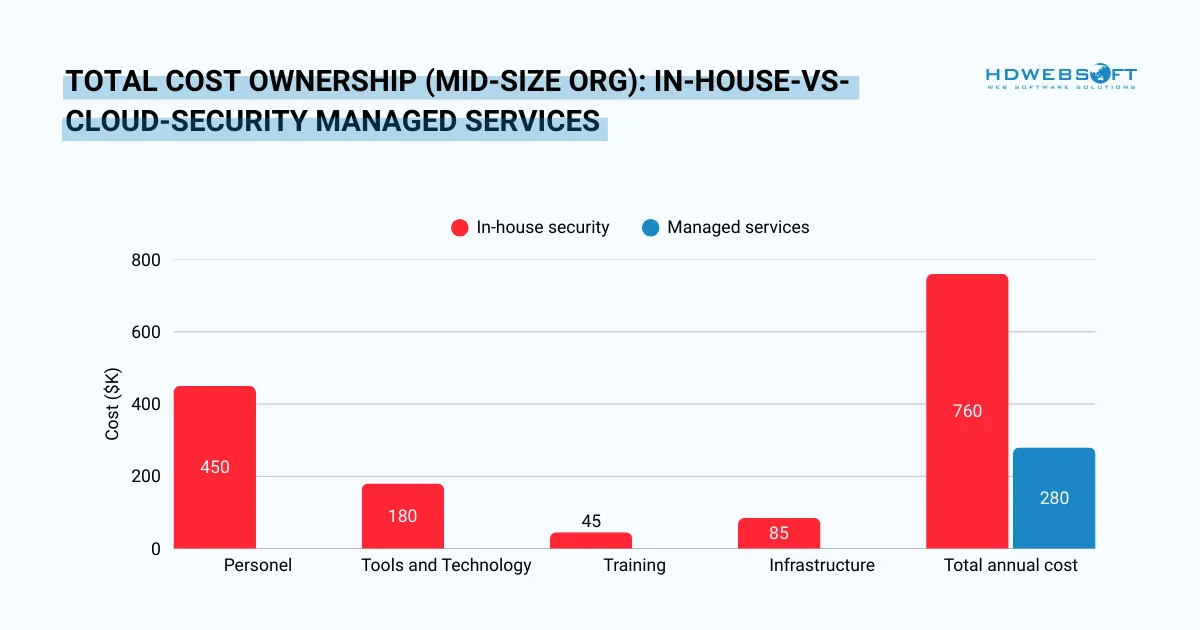
Cost Predictability Versus Building In-House
Internal security teams require substantial ongoing investment beyond initial hiring costs. Turnover, training, tools, and infrastructure create unpredictable expenses.
Cloud security managed services operate on subscription models with transparent pricing. Therefore, organizations can budget accurately and avoid surprise costs. Additionally, providers absorb technology refresh cycles and tool licensing within their service fees.
How MSPs Ensure Secure Cloud Storage
Data protection forms the foundation of any managed cloud security services strategy. Meanwhile, storage security encompasses multiple layers working together to prevent unauthorized access and data loss. Organizations using these managed services benefit from automated encryption, access controls, and continuous monitoring.
Encryption Standards and Implementation
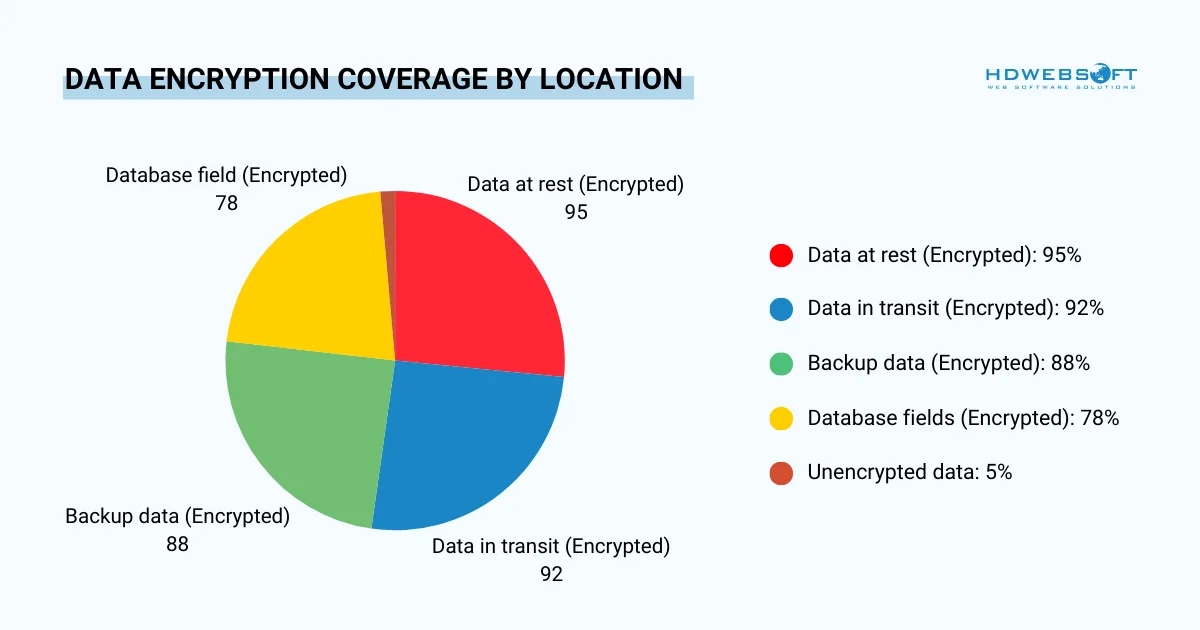
Data encryption protects information both when stored and during transmission between systems. Managed security service providers implement encryption automatically across your cloud infrastructure. In addition, industry-standard protocols ensure data remains unreadable even if physical storage media falls into wrong hands.
Standard encryption practices
- AES-256 encryption for data at rest
- TLS 1.3 for data in transit
- Encrypted backups with separate key management
- Client-side encryption for highly sensitive data
- Database-level encryption for structured data
- Field-level encryption for specific sensitive attributes
Key management represents a critical component often overlooked by organizations. Consequently, cloud security managed services use hardware security modules (HSMs) or cloud-native key management services to protect encryption keys. This is because proper key rotation schedules further strengthen encryption effectiveness. Moreover, separation of duties ensures no single administrator controls both data and encryption keys.
Access Controls and Identity Management
Limiting who can access sensitive data prevents both external breaches and insider threats. Identity and access management (IAM) creates granular control over resource permissions. Meanwhile, modern zero-trust architectures assume no user or system automatically deserves access.
Managed cloud security providers implement least-privilege access principles where users receive only necessary permissions. Furthermore, they enforce multi-factor authentication (MFA) across all administrative accounts. Regular access reviews ensure permissions stay current as roles change. Finally, time-based access grants additional security by automatically revoking elevated permissions after specified periods.
Moreover, role-based access control (RBAC) simplifies permission management across large organizations. To the cloud security managed services’ suggestion, instead of assigning individual permissions, administrators grant predefined roles matching job functions. Attribute-based access control (ABAC) provides even finer granularity based on user attributes, resource characteristics, and environmental conditions. And privileged access management (PAM) solutions add extra protection for high-risk administrative accounts.
Data Loss Prevention Strategies
Accidental deletion, ransomware, and system failures threaten data availability. That’s why comprehensive protection requires multiple safeguards working in concert.
DLP measures
- Automated backup scheduling with retention policies
- Immutable backup storage preventing tampering
- Geographic replication across multiple regions
- Regular restoration testing to validate backup integrity
- Version control allowing recovery to specific points in time
Backup and Disaster Recovery
Business continuity depends on rapid recovery from catastrophic events. Managed service providers for cloud security design disaster recovery (DR) plans tailored to your recovery objectives.
Recovery Time Objective (RTO) defines how quickly systems must return to operation. Meanwhile, Recovery Point Objective (RPO) determines acceptable data loss measured in time. Cloud security managed services architect backup strategies meeting these specific targets.
Regular Security Assessments and Audits
Continuous validation ensures security controls function as intended and adapt to emerging threats. In fact, assessments identify gaps before attackers can exploit them.
Quarterly vulnerability scans detect weaknesses in cloud configurations and applications. Additionally, annual penetration tests simulate real-world attacks against your environment. Your providers’ remediate findings and track improvements over time.
Cloud Security Posture Management in Managed Services
Maintaining secure configurations across dynamic cloud environments challenges even experienced teams. Cloud security posture management (CSPM) tools automate this critical function within service range. For that reason, modern managed cloud security services incorporate CSPM to ensure continuous compliance and rapid remediation.
What CSPM Tools Monitor
Cloud resources change constantly as teams deploy new workloads and modify existing configurations. CSPM solutions continuously scan your environment for security issues.
Key monitoring capabilities
- Misconfigured storage buckets exposed to public internet
- Overly permissive IAM policies granting excessive access
- Encryption disabled on databases or storage volumes
- Network security groups allowing unrestricted inbound traffic
- Compliance violations against CIS benchmarks or custom policies
These tools integrate with major cloud platforms including AWS, Azure, and Google Cloud. Therefore, they provide unified visibility regardless of where workloads run.
How Managed Services Leverage CSPM
Cloud security managed services incorporate CSPM platforms as part of comprehensive protection strategies. Providers configure these tools to match your specific security and compliance requirements.
For example, AWS Security Hub aggregates findings from multiple security services and third-party solutions. Managed providers correlate these alerts with broader threat context to prioritize remediation. Similarly, Azure Security Center provides recommendations that align with industry frameworks.
Expert teams interpret CSPM findings to separate critical risks from informational alerts. Additionally, they validate automated detections through manual investigation when needed.
Continuous Compliance Monitoring
Regulatory frameworks like SOC 2, ISO 27001, and GDPR require ongoing evidence of security controls. Manual compliance tracking consumes significant resources and introduces human error.
CSPM platforms map cloud configurations to specific compliance requirements automatically. Consequently, organizations maintain audit-ready documentation without manual effort. Real-time compliance dashboards show current status against multiple frameworks simultaneously.
Automated Remediation Capabilities
Detecting security issues quickly matters little if remediation takes days or weeks. Hence, cloud security managed services leveraging automated response capabilities within CSPM tools to fix common misconfigurations immediately.
Remediation examples
| Issue Detected | Automated Response |
| Public S3 bucket | Apply private access controls |
| Missing encryption | Enable encryption with managed keys |
| Excessive permissions | Reduce to least-privilege access |
| Open security group | Restrict to approved IP ranges |
| Untagged resources | Apply standard tagging schema |
Manual approval workflows ensure critical changes receive human oversight before implementation. Therefore, automation balances speed with appropriate control.
Choosing the Right Cloud Security Managed Service Provider
Selecting a managed cloud security provider requires careful evaluation of capabilities, experience, and cultural fit. The right partnership strengthens your security posture significantly. Poor provider selection, however, can create new vulnerabilities while failing to address existing risks.
Provider maturity varies dramatically across the managed security landscape. Some offer comprehensive enterprise-grade services while others provide basic monitoring with limited response capabilities. Therefore, understanding these differences helps organizations avoid costly mismatches between needs and provider offerings.
Key Evaluation Criteria
Provider assessment should examine both technical capabilities and business factors. Notably, cloud security managed services vary widely in scope and quality.
Essential selection factors
- Certifications: SOC 2 Type II, ISO 27001, CSA STAR, and ISO 27001 certification.
- Cloud expertise: Demonstrated experience with your specific cloud platforms.
- Industry knowledge: Understanding of your sector’s regulatory requirements.
- Technology stack: Modern security tools and threat intelligence capabilities.
- SLA commitments: Guaranteed response times and uptime percentages.
- Scalability: Ability to grow services as your needs expand.
Client references provide valuable insight into day-to-day partnership experiences. Additionally, case studies demonstrate problem-solving approaches for challenges similar to yours.
Questions to Ask Potential Providers
Thorough vetting conversations reveal how providers operate beyond marketing materials. Direct questions to your cloud security managed services help assess cultural alignment and operational practices.
Security Operations
- How many security analysts will monitor our environment?
- What is your average detection and response time for critical threats?
- How do you handle security incidents during off-hours and holidays?
Reporting and Communication
- What metrics and KPIs do you provide in regular reports?
- How often will we meet to review security posture and findings?
- Who serves as our primary point of contact for issues?
Technology and Integration
- Which security tools and platforms do you use?
- How do your systems integrate with our existing infrastructure?
- Can we access security data and dashboards directly?
Red Flags to Watch For
There are certain warning signs that indicate providers may not deliver promised capabilities. Hence, it’s important to recognize these concerns early to prevent costly mistakes.
Avoid providers who
- Cannot provide client references or detailed case studies
- Offer vague answers about their security tools and processes
- Promise unrealistic results or guaranteed breach prevention
- Lack relevant certifications or compliance attestations
- Use exclusively offshore teams for critical security functions
- Require long-term contracts without trial periods
Transparency in methodologies and honest communication about limitations indicate trustworthy partnerships. Furthermore, providers should acknowledge that cloud security managed services reduce risk rather than eliminate it entirely.
Conclusion
Managed cloud security services provide organizations with expert protection against increasingly sophisticated cyber threats. By outsourcing security operations, businesses gain 24/7 monitoring, rapid incident response, and access to specialized expertise. Successful implementations reduce risk while optimizing security budgets.
The right provider delivers comprehensive protection across your cloud environment while ensuring compliance with regulatory requirements. Moreover, predictable costs and scalable services make managed security accessible to organizations of all sizes.
Ready to strengthen your cloud security posture? Contact our team to discuss how HDWEBSOFT’s cybersecurity services can protect your organization’s critical assets and data.