The 2025 State of Connected Car Cybersecurity
Connected car cybersecurity is a paramount concern as the automotive industry undergoes a monumental transformation. It’s shifting from a focus on mechanical prowess to a sophisticated ecosystem driven by data, software, and ubiquitous connectivity. As we rapidly move into 2025, these vehicles are evolving into complex, rolling computers offering convenience, safety, and efficiency. From advanced infotainment systems and real-time navigation to crucial over-the-air (OTA) updates and autonomous driving capabilities, the benefits are undeniable.
However, this profound interconnectedness also introduces a vast and intricate web of vulnerabilities, making cybersecurity a critical imperative. A single breach could escalate from a mere inconvenience to jeopardize occupant safety and public trust. In this blog, we examine the primary cybersecurity challenges, potential risks, and the necessary steps automakers must take to ensure the security of connected vehicles.
The Evolving Threat Landscape in Connected Car Cybersecurity
As the market for connected cars continues to expand rapidly, vehicles are becoming more than just transportation—they’re complex, data-driven systems integrated with the broader digital ecosystem.
The image below highlights the projected growth of the connected car market from 2023 to 2034, reflecting the increasing adoption and integration of smart automotive technologies.
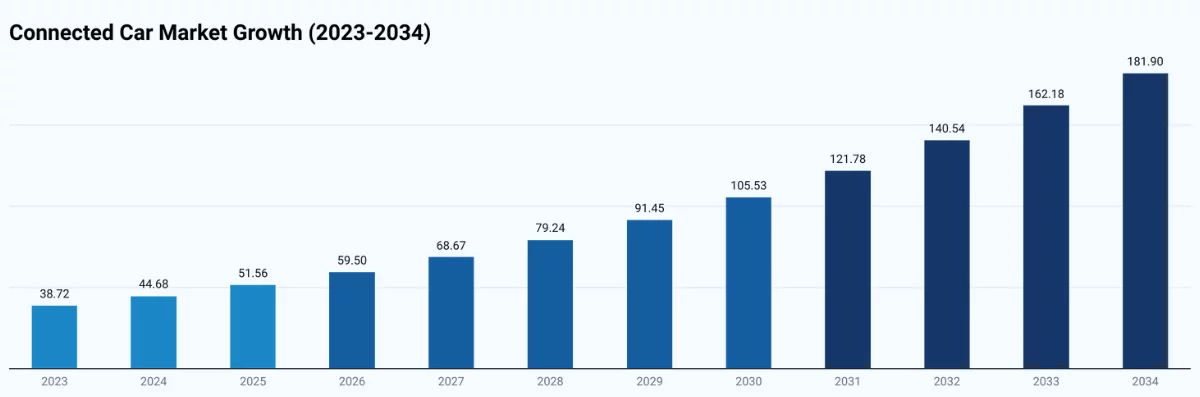
Collected data from Precedence Research.
The intricate architecture of modern IoT-connected cars, coupled with their constant interaction with external networks and infrastructure, creates a fertile ground for a diverse array of cyber threats. Understanding these evolving attack vectors is the first step in fortifying connected car cybersecurity.
Expanding Attack Surfaces
The volume of data exchange and components within and around a connected car significantly expands its potential attack surface:
Vehicle-to-Everything (V2X) Communication
This is arguably the broadest attack surface. V2X enables cars to communicate with other vehicles (V2V) and infrastructure (V2I), like smart traffic lights. It also supports communication with pedestrians (V2P) via mobile devices and with cloud networks (V2N).
Hence, exploiting vulnerabilities in these communication protocols (e.g., DSRC, C-V2X) could lead to various malicious scenarios. They include jamming critical safety warnings and manipulating traffic flow for illicit gains. Consequently, they all pose a direct threat to cybersecurity for connected cars.
In-Vehicle Network Protocols
Modern vehicles are mini-networks themselves, often housing dozens, sometimes hundreds, of Electronic Control Units (ECUs) controlling everything from engine management to power windows. These ECUs communicate via protocols like CAN bus, FlexRay, Automotive Ethernet, and LIN.
That’s why a compromise of any single ECU could pose a serious threat. Injecting malicious messages onto the network might let attackers gain unauthorized control over critical vehicle functions. This makes robust connected car cybersecurity for internal networks absolutely vital.
External Interfaces and Connectivity Modules
Bluetooth, Wi-Fi, cellular (4G/5G), and USB ports offer convenient entry points. However, if attackers exploit flaws in infotainment systems or telematics control units (TCUs), they can gain a foothold. Additionally, vulnerabilities in the diagnostic port (OBD-II) can open doors for unauthorized access or malware injection.
Maybe you haven’t read: Network Signalling Specialist Flags 5G Security Concerns.
Mobile Applications and Cloud Services
Many connected car features are managed via smartphone apps and cloud-based backend services. Weaknesses in cloud infrastructure, API security, or even user authentication processes can lead to remote vehicle access, data theft, or privacy breaches.
Sophisticated Cyber Threats
The nature of cyber threats targeting connected cars is becoming increasingly sophisticated, demanding advanced connected car cybersecurity measures:
Remote Exploitation and Manipulation
Beyond simple data theft, the primary concern is the ability of attackers to remotely control vehicle systems. Resultantly, this could involve disabling brakes, accelerating, steering, or even locking occupants inside, presenting an existential threat to safety.
Data Exfiltration and Privacy Invasion
Connected cars collect a treasure trove of data. They can be location history, driving habits, biometric data (from in-cabin cameras and sensors), infotainment usage, and even passenger conversations.
Thus, this highly sensitive data is a lucrative target for identity theft, blackmail, or resale on the dark web. Ultimately speaking, data privacy is a key pillar of cybersecurity for connected cars.
Ransomware and DoS Attacks

Imagine a scenario where a car’s systems are locked down by ransomware, demanding payment to restore functionality. In another case, a DoS attack could render an entire fleet of vehicles inoperable, leading to massive economic disruption.
As these threats become more real, connected car cybersecurity is a growing concern for both fleet operators and individual owners.
Supply Chain Vulnerabilities
The automotive supply chain is a global and complex network, involving numerous tiers of hardware and software suppliers. A single vulnerability introduced at any point in this chain, whether in a third-party software component, an embedded chip, or a diagnostic tool, can have serious consequences.
Once exploited, it can quickly propagate across millions of vehicles. As a result, it creates a widespread systemic risk that challenges traditional cybersecurity defenses for connected cars.
“Carjacking” through Digital Means
This new form of car theft involves bypassing traditional security (like key fobs) using digital exploits, cloning key signals, or exploiting vulnerabilities in remote access systems.
Pillar Strategies for Robust Cybersecurity for Connected Cars
Addressing the multifaceted threat landscape requires a comprehensive and multi-layered approach to cybersecurity for connected cars. The industry is focusing on several key strategic pillars:
Security-by-Design and Shift-Left Principles
Instead of patching connected car cybersecurity flaws after development, the industry is increasingly adopting a security-by-design philosophy.
- Integrating Security from Inception: This means that cybersecurity considerations are baked into every stage of the vehicle’s lifecycle. At each phase, architects and engineers assess potential threats and implement countermeasures early on.
- Secure Software Development Lifecycle (SSDLC): This involves rigorous code reviews, static and dynamic analysis, penetration testing, and vulnerability assessments throughout the software development process. As a matter of fact, these strategies significantly reduce the introduction of exploitable flaws.
- Threat Modeling and Risk Assessment: Before any system is built, detailed threat models are created to identify potential attack vectors and assess the risks associated with various components and interactions. Then, these models guide the implementation of appropriate controls.
Hardware-Level Security and Trust Anchors
The foundation of connected car cybersecurity often lies in the hardware itself.
- Trusted Execution Environments (TEE): These isolated processing environments within a chip provide a secure space for sensitive operations. This separation helps protect them from vulnerabilities in the main operating system.
- Hardware Security Modules (HSM): These are dedicated hardware components designed to store and protect cryptographic keys and perform cryptographic operations. They ensure the integrity and authenticity of data and software.
- Secure Boot and Firmware Updates: Ensuring that only authenticated and uncompromised firmware can load at startup is critical. Hence, secure boot mechanisms verify the digital signature of each piece of software before it executes, preventing malicious code from taking control.
Advanced Intrusion Detection and Prevention Systems (IDPS)
Real-time monitoring and rapid response are crucial for cybersecurity for connected cars.
- In-Vehicle IDPS: They are systems that continuously monitor internal network traffic (e.g., CAN bus), ECU behavior, and software execution. They look for anomalies that might indicate an intrusion, playing a vital role in connected car cybersecurity. Leveraging AI and Machine Learning, these systems can learn normal vehicle behavior and flag deviations.
- Cloud-Based Monitoring and Analytics: Telematics data streamed to the cloud can be analyzed centrally using big data analytics and AI. This helps identify widespread attack patterns, zero-day exploits, or coordinated threats across entire fleets.
- Automated Threat Response: Beyond detection, the goal is to enable automated responses. The actions include isolating compromised ECUs, logging events, or even triggering an alert to the driver or a remote security operations center (SOC)
The Role of Over-the-Air (OTA) Updates and Data Privacy
There are two critical aspects profoundly influencing cybersecurity for connected cars in 2025. They are the secure management of OTA updates and the robust protection of user data.
Securing OTA Updates
OTA updates are a double-edged sword. On one side, they offer unparalleled convenience for delivering bug fixes and new features. On the other side, they also represent a potential massive attack vector to connected car cybersecurity if not secured rigorously.
Cryptographic Signatures and Authentication
Every OTA update package must be digitally signed by the manufacturer using strong cryptographic keys. Therefore, vehicles must be able to authenticate these signatures before accepting and installing any update.

Secure Communication Channels
Updates must be delivered over encrypted and authenticated communication channels (e.g., HTTPS, TLS) to prevent interception or tampering during transit.
Rollback Mechanisms and Failsafes
Robust OTA systems are designed with safeguards to ensure reliability. Namely, if an update fails or introduces critical bugs, it includes mechanisms to revert to a previous, stable software version. And ultimately, the goal is to prevent vehicle bricking.
Granular Update Control
Manufacturers are developing more granular control over updates, enabling targeted deployments to specific vehicle models or regions. Additionally, they now have the ability to pause or halt updates immediately if any issues arise. This is crucial for maintaining the integrity of cybersecurity for connected cars.
Data Privacy and Compliance
With the immense amount of data generated by connected cars, privacy is a major connected car cybersecurity concern.
Data Minimization
This involves collecting only the data that is absolutely necessary for the functionality of the vehicle or service. Additionally, data should be anonymized or pseudonymized whenever possible to enhance privacy protection.
Consent Management
Manufacturers must provide clear, transparent mechanisms for users to understand what data is being collected and how it will be used. Furthermore, users should be able to grant or revoke consent for data sharing at any time.

Compliance with Regulations
Adhering to stringent data protection regulations like GDPR, CCPA, and emerging automotive-specific privacy laws. This includes ensuring data sovereignty and proper handling of cross-border data transfers.
Robust Encryption
End-to-end encryption should be implemented for data both in transit and at rest. This protects the data from unauthorized access, whether it’s stored in the vehicle’s local memory or in cloud backend systems.
Transparency and User Control
Drivers should be empowered with dashboards or apps that let them visualize, view, and manage their collected data. In addition, they should have the option to delete that data, fostering greater trust in cybersecurity for connected car practices.
Collaboration, Standards, and the Future of Connected Car Cybersecurity
The complexity of connected car cybersecurity means no single entity can tackle it alone. Collaboration, standardized frameworks, and continuous innovation are essential for success.
Industry Collaboration and Information Sharing
Automotive ISACs (Information Sharing and Analysis Centers)
Organizations like Auto-ISAC facilitate the sharing of threat intelligence, best practices, and vulnerability information among manufacturers, suppliers, and security researchers. This collective defense approach significantly strengthens the overall posture of cybersecurity for connected cars.
Bug Bounty Programs
In fact, manufacturers are increasingly engaging ethical hackers through bug bounty programs, offering rewards for responsibly disclosing vulnerabilities. Consequently, this leverages the expertise of the global security community to identify flaws before malicious actors can exploit them.
Partnerships with Cybersecurity Experts
Collaborating with specialized cybersecurity firms brings deep expertise in areas like penetration testing, incident response, and security architecture design. These partners not only help identify and mitigate vulnerabilities but also bring mastery of advanced cybersecurity tools. They’ll make sure of comprehensive protection for connected vehicles.
Regulatory Frameworks and International Standards
Governments and international bodies are playing an increasingly active role in shaping connected car cybersecurity.
UN Regulation No. 155 (UN R155)
This groundbreaking regulation by the United Nations Economic Commission for Europe (UNECE) sets a new global standard. It mandates that vehicle manufacturers establish and implement a certified Cybersecurity Management System (CSMS) across their entire vehicle lifecycle. Overall, it’s a significant step towards global standardization of cybersecurity for connected car requirements.
ISO/SAE 21434
This international standard provides a framework for cybersecurity engineering within the road vehicle lifecycle, offering guidelines for managing cybersecurity risks. Moreover, it’s often used in conjunction with UN R155 to ensure comprehensive compliance and protection.
Regional Legislation
Beyond global standards, individual countries and blocs, such as the EU and the US, are introducing their own specific laws and guidelines. These efforts aim to strengthen cybersecurity further and enhance consumer protection.
Continuous Adaptation and Future Challenges
The battle for connected car cybersecurity is an ongoing one, requiring constant adaptation.
Quantum Computing Threats
As quantum computing advances, it poses a long-term threat to current cryptographic algorithms. Thus, research into post-quantum cryptography is already underway to prepare for the future challenge of cybersecurity for connected cars.
AI-Powered Attacks and Defenses
In fact, AI can be used by both attackers and defenders in the realm of cybersecurity.
For example, attackers might use it to generate sophisticated malware or bypass detection systems. On the other hand, defenders can leverage AI for anomaly detection, predictive analysis, and automated response.
Digital Twins and Simulation
Leveraging digital twins, virtual replicas of physical vehicles, can greatly enhance cybersecurity and AI testing. They allow for rapid iteration and vulnerability discovery in a simulated environment, without putting physical assets at risk.
The Transition to Full Autonomy
As vehicles move towards higher levels of autonomy, the potential impact of a cyberattack becomes even more critical. Therefore, trust in the autonomous system’s integrity is paramount, placing immense pressure on connected car cybersecurity solutions.
Conclusion
The connected car revolution promises a future of unprecedented convenience and safety. However, realizing this potential fully depends on an unyielding commitment to connected car cybersecurity. It’s not just about safeguarding data or preventing theft; it’s about protecting lives and maintaining trust in a technology that’s rapidly becoming central to our daily lives.
With a strong emphasis on protection and performance, HDWEBSOFT combines software development expertise with professional cybersecurity services to help businesses operate confidently online. Reach out to explore how we can support your digital initiatives.