Network signaling specialist flags 5G security concerns
The advent of 5G technology promises to revolutionize various sectors, from healthcare and transportation to smart cities and entertainment. With its high-speed data transfer, low latency, and ability to connect millions of devices, 5G is set to transform how we live and work.
However, alongside these benefits come significant security concerns, as highlighted by a leading network signaling specialist. This article delves into the potential security risks associated with 5G and underscores the need for robust mitigation strategies.
Overview of 5G Technology

5G, the fifth generation of mobile networks, offers unprecedented speed and connectivity. It is designed to support a vast number of devices simultaneously, facilitating the growth of the Internet of Things (IoT). Unlike its predecessors, 5G uses higher frequency bands and advanced technologies such as beamforming and network slicing to deliver faster data rates and lower latency.
The Benefits of 5G Technology
The benefits of 5G are extensive. It enables real-time remote surgery, autonomous vehicles, enhanced virtual and augmented reality experiences, and much more. Compared to 4G, which offers peak download speeds of 1 Gbps, 5G can reach up to 20 Gbps. We can expect this leap in performance to drive innovation and economic growth across various industries.
Identified Security Concerns in 5G Technology
5G technology promises a revolution in mobile connectivity, with faster speeds, lower latency, and the ability to connect a wider range of devices. However, with this advancement comes a new set of security challenges that must be addressed.
Let’s take a look at an example from NCC Group about attack scenarios against a typical 4G/5G mobile network before delving into the key identified security concerns in 5G:
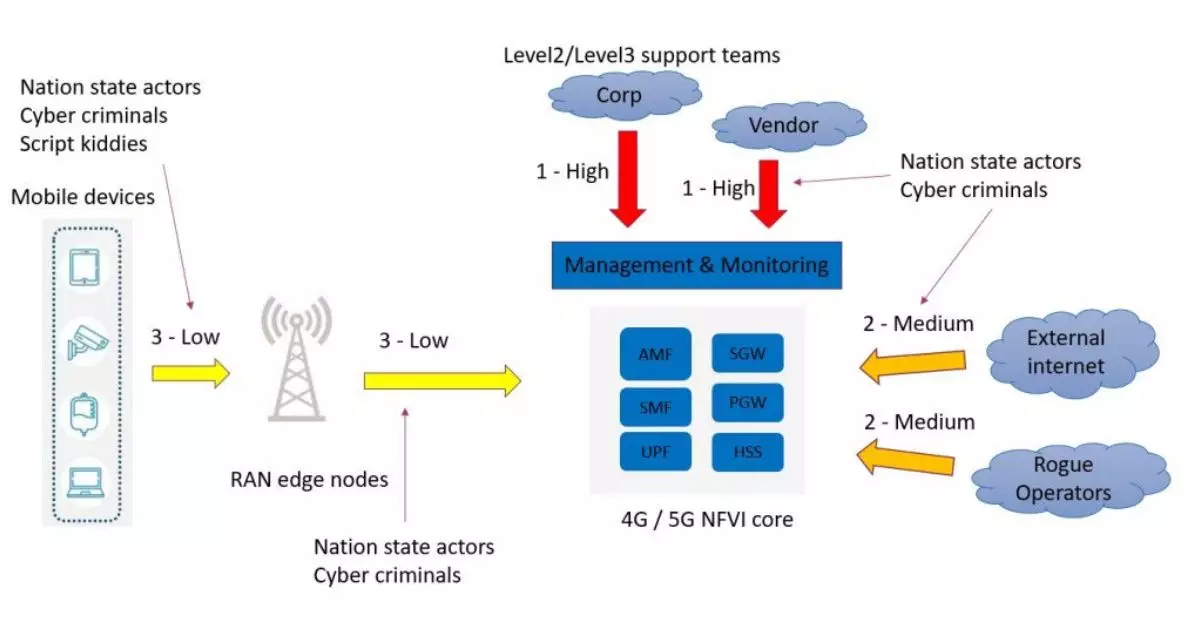
Increased Attack Surface
The expansive connectivity of 5G networks introduces a larger attack surface for cybercriminals. The integration of billions of IoT devices, from smart home appliances to industrial sensors, creates numerous potential entry points for attacks.
According to a report by Gartner, there will be 25 billion connected devices by 2025, significantly increasing the risk of cyber threats. The diversity and scale of these devices make it challenging to implement uniform security measures, making them prime targets for hackers.
Network Slicing Risks
Network slicing allows multiple virtual networks to run on the same physical infrastructure, each tailored to specific applications or services. While this enables efficient resource utilization and customized service delivery, it also poses significant security challenges.
For instance, each slice can have different security requirements, and isolating them to prevent cross-slice attacks is complex. Misconfigurations or vulnerabilities in one slice could potentially compromise the entire network.
Supply Chain Security
The reliance on a diverse supply chain for hardware and software components introduces risks related to the integrity and security of these elements. The global nature of 5G technology means that components are sourced from various countries, each with different security standards and practices.
Concerns about backdoors and vulnerabilities in foreign-sourced equipment have led to increased scrutiny and calls for more stringent supply chain security measures. Blockchain technology, with its tamper-proof ledger system, has emerged as a potential solution for securing the 5G supply chain by ensuring the provenance and authenticity of components at every stage. According to a report by the CISA, 45% of companies reported supply chain-related cyber incidents in the past year, underscoring the urgency of addressing this issue.
Encryption and Data Privacy
The high volume of data transmitted over 5G networks necessitates robust encryption to protect user privacy and sensitive information. However, current encryption standards may not be sufficient to counter advanced cyber threats.
As data moves seamlessly across various devices and networks, ensuring end-to-end encryption and maintaining data integrity becomes increasingly challenging. Still, the potential for man-in-the-middle attacks and data breaches is a significant concern that requires ongoing attention.
Regulatory and Standardization Issues
The global implementation of 5G requires consistent security standards and regulations across different regions and providers. Yet, achieving uniform security protocols is challenging due to varying regulatory environments and levels of technological advancement.
Moreover, the lack of standardized security measures can lead to vulnerabilities and inconsistencies that cybercriminals can exploit. Therefore, coordinated efforts between governments, international organizations, and industry stakeholders are essential to establish comprehensive security frameworks.
Expert Insights on 5G Security Concerns

A network signaling specialist paints a concerning picture of the real-world implications of these 5G security vulnerabilities that are left unaddressed. Imagine widespread disruptions to critical services – power grids, transportation systems, even emergency response networks – all potentially halted by a cyberattack exploiting weaknesses in the 5G infrastructure. The consequences extend far beyond inconvenience, with potential data breaches exposing sensitive information and causing significant financial losses for businesses and individuals.
This specialist emphasizes the urgency of a proactive approach. Collaboration between governments, network operators, and technology companies is vital. By working together to develop and implement robust security measures, we can safeguard the integrity and confidentiality of data on 5G networks, ensuring that this powerful technology fulfills its promise of a connected future without compromising security.
Mitigation Strategies for 5G Security Concerns

Addressing 5G security concerns requires a multifaceted approach. Governments, telecom providers, and technology companies must work together to implement effective security measures. Recommended strategies include:
- Enhanced Encryption: Developing and deploying advanced encryption techniques to protect data integrity and privacy.
- Supply Chain Security: Implement stringent security standards for all components and conduct regular audits to ensure compliance.
- Network Slicing Security: Establishing robust isolation protocols and continuous monitoring to prevent cross-slice attacks.
- Standardization: Collaborating on global standards to ensure consistent security practices across regions.
Let’s see how HDWEBSOFT handles Security concerns in a social network app.
Conclusion
As 5G technology continues to evolve and integrate into our daily lives, addressing its security challenges becomes paramount. The insights from the network signaling specialist underscore the importance of proactive measures and collaboration among stakeholders.
By focusing on enhanced encryption, supply chain security, network slicing protection, and standardized protocols, we can mitigate the risks associated with 5G and unlock its full potential for a secure and connected future.